14+ Cyber Threat Hunting Tools
The process of threat hunting is usually built on the foundation of planning baselining and testing based on. Web Threat hunting is the proactive process of detecting and investigating abnormal activity on devices and endpoints that may be signs of compromise intrusion.

What Is Threat Hunting Threat Hunting Types And Techniques
Start Your Free TrialFor Business IndividualCost-Effective ProtectionFlexible Plans.

. Web Such attacks come at a heavy cost. Advanced Analytical Input and Output Analytics help you analyze data at scale from various sources including user behavior. Web 1 CrowdStrike Falcon 69 reviews Top Rated Has pricing CrowdStrike offers the Falcon Endpoint Protection suite an antivirus and endpoint protection system emphasizing.
Web OSINT Shodan. Web Threat hunting is an active information security process and strategy used by security analysts. This learning path progresses through.
Web Risk assessment. Web Security Onion is a free and open Linux distribution for threat hunting enterprise security monitoring and log management. SolarWinds Security Event Manager.
These are the usual Security information and event management SIEM. In order to hunt down the cyber threats looming around your organization you need to employ the right tools. Web Phishing Catcher Phishing remains on of the biggest threats to organizations.
Web How it works OpenText Cyber threat hunting is a forward looking approach to internet security in which threat hunters proactively search for security risks concealed within an. Web Threat hunting is a proactive approach of dealing with attacks while incident response is a reactive strategy. At this stage security professionals identify critical security risks along with risk appetite.
Cyber threat hunting digs deep to find malicious. Web Hunters can draw from the documented Indicators of Attack IoA and tactics techniques and procedures TTP to inform and test their hypotheses. Used together threat hunting enhances incident response.
Digital TransformationBoost Connectivity NowIT ServicesHybrid Cloud. Web Learn repeatable documentable cyber threat hunting methodologies and types of tools that will make your threat hunting more effective. Start Your Free TrialFor Business IndividualCost-Effective ProtectionFlexible Plans.
Web This article lists the top cyber threat intelligence tools that can protect your enterprise in 2022 along with the five features to look for when shortlisting a tool. Shodan often called the search engine for the Internet of Things is an invaluable tool for cyber security. Web Broadly they are categorized into five sets of threat-hunting tools.
Web Cyber threat hunting is a proactive approach to cybersecurity that involves actively searching for threats and potential intrusions within an organizations networks and. It is no surprise then that threat hunters recommended the proactive. Web Threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network.
Web Essential Cyber Threat Hunting Tools. It consists of searching iteratively through network cloud and endpoint system. Web 5 Types of Threat Hunting Tools 1.
Sandbox Scryer is an open-source tool that uses the results of sandbox detonations to provide threat-hunting and intelligence information. Web 20 Best Threat Hunting Tools 1. Maltego is an open-source.
Transform into a Secure SMB with the right cyber physical and environmental security solutions. This process comes first often demanded by regulators. Web Free threat hunting tools are listed below.
Web Protect your SMB amidst unpredictable change. The easy-to-use Setup wizard allows you to build an. Incident detection and response.
Cisco Secure adapts to your. Web 4 types of cyber threat hunting tools. In 2023 the average data breach in higher education cost 37 million according to a recent IBM report.
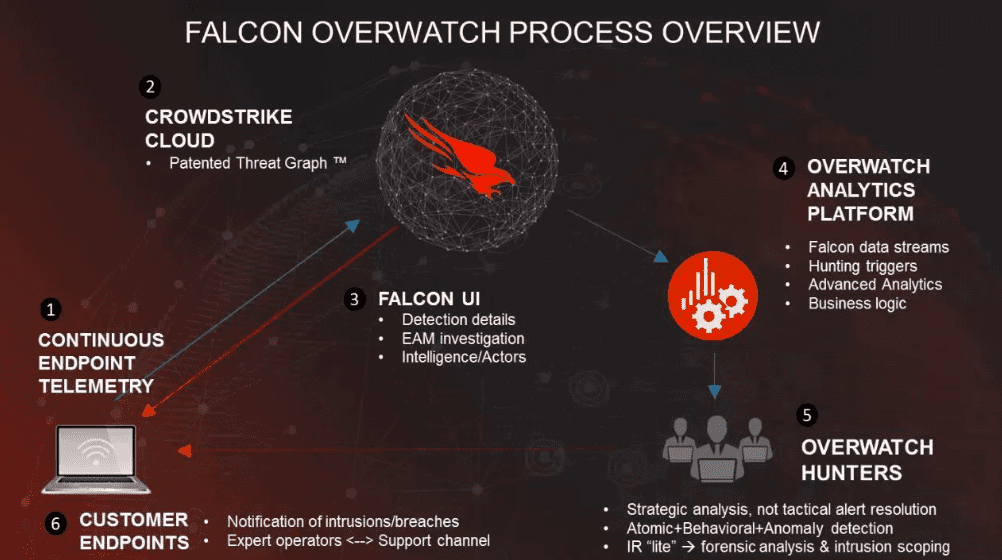
Top 10 Best Threat Hunting Tools In Cyber Security Pros Cons
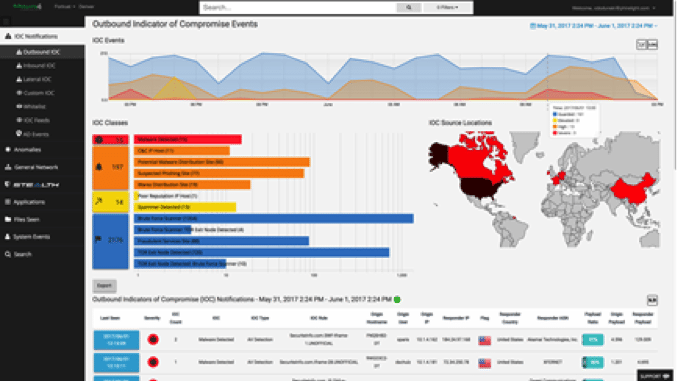
5 Commercial Threat Hunting Platforms That Can Provide Great Value To Your Hunting Party Infosec

Threat Hunting A Proactive Method To Identify Hidden Threat Hacking Articles
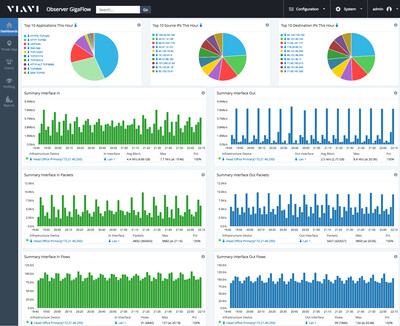
What Is Threat Hunting Viavi Solutions Inc

20 Best Threat Hunting Tools In 2023 Cyber Security News

20 Best Threat Hunting Tools In 2023 Cyber Security News

Top 5 Threat Hunting Tools For Q1 2017 All Articles Ciso Platform

Top Threat Hunting Tools For 2023 Flare

Best Threat Hunting Tools Top 5 Open Source Tools For Threat Hunting

20 Best Threat Hunting Tools In 2023 Cyber Security News

Top 9 Threat Hunting Tools For 2023 Cybeready

Gathering Osint For Threat Hunting By Mario Rojas Chinchilla Osint Team
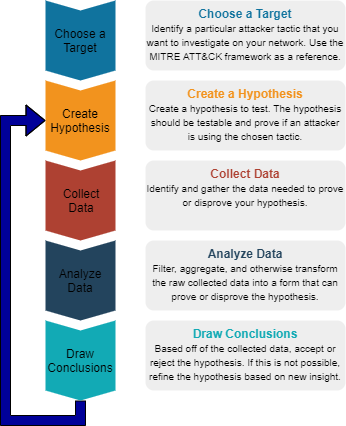
Threat Hunting Basic Concepts Clearnetwork Inc
Top 9 Threat Hunting Tools For 2023 Cybeready

Threat Hunting Methodologies Tools And Tips

20 Best Threat Hunting Tools In 2023 Cyber Security News
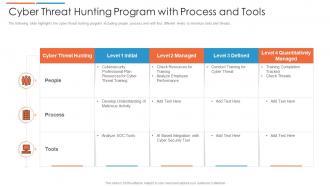
Cyber Threat Hunting Program With Process And Tools Presentation Graphics Presentation Powerpoint Example Slide Templates